Remote Work Software: The Sortable List (2023)
If you run a remote team or work from home, this is THE GUIDE FOR YOU. We keep it updated, too (and ask for contributions down here).
This list includes 79 software tools for remote work organized by type of tool, how it’s priced, and my personal favorites (if anyone cares). You can filter the list any way you’d like. I asked over 80 people who work from home for their absolute most useful remote tool, and built this resource from their input.
Start by filtering categories below.
Here are your results.
🔗 Automation Software
Here are the applications that are primarily categorized as automation tools. Keep in mind that the automation tools we feature are specifically to help for remote teams and employees. Others, like Taskeo, have covered business automation tools in much more detail than me. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Zapier
| 🔗 Automation | 💸 Freemium 👍 Henry’s Favorite |
Zapier is a powerful automation tool that lets you connect multiple third party apps and services in order to automate workflows.
Best Feature: Zapier can connect 2,000+ applications. “For example, I use Zapier to find and validate emails for our outreach campaigns. It allows me to connect Google Sheets, Hunter.io (email finder), Neverbounce (email validator), and Mailshake (outreach tool). It results in a smooth running workflow.”
Thank you Ivan Ambrocio, the co-founder of the blog constantlystriving.com, for sharing his favorite automation tool.
Visit The Website:
https://zapier.com/
See Also: Hybrid Work Software Tools
Fyle
| 🔗 Automation | 🤝 Collaboration | ⚙️ Productivity | 🗂 Document Management | 💰 Paid |
Fyle is an expense management software that enables you to take control of company-wide business expenses.
Unique Feature: Fyle the first expense management solution to offer direct card feeds for any Visa or Mastercard powered credit card from any bank. This makes reconciling credit card expenses a breeze for your finance teams.
Visit The Website:
https://www.fylehq.com/
See Also: 4-day week & remote software engineer jobs
📅 Calendar Tools
Here are the applications that are primarily categorized as calendaring tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Calendly
| 📅 Calendar ⚙️ Productivity 🔗 Automation | 💸 Freemium 👍 Henry’s Favorite |
Stop sending emails back and forth trying to figure out a time to meet. Calendly allows you to offer a way for people to book a meeting with you that won’t conflict with anything already on your calendar.
Unique Feature: Control your availability by entering hours in which you are willing to accept meetings. This adds a layer beyond what’s already booked on your calendar. For example, if you prefer meeting mornings, you can set your availability only during those times.
Visit The Website:
https://calendly.com
Calendar.com
| 📅 Calendar ⚙️ Productivity | 💸 Freemium |
Calendar.com is a productivity tool that gives you insight into how many meetings you have, how many you have scheduled, how many were cancelled, and how many were missed.
Unique Benefit: “It shows you how much time you spend in meetings, and visualizes other productivity metrics to help you create smarter meetings and spend less time in them. It’s great for remote teams because we all have so many meetings with other remote team members!”
Thank you Jayson DeMers, CEO of EmailAnalytics, for sharing his team’s calendaring tool of choice.
Visit The Website:
https://www.calendar.com/
CommandDot
| 📅 Calendar ⚙️ Productivity | ❓ Unknown Price |
You know how meeting scheduling usually starts as a back-and-forth over email? CommandDot allows you to book meetings right there in your inbox based on the conversation you are having in the email.
Unique Benefit: You can book a meeting much, much faster than any way before.
Visit The Website:
https://commanddot.com/
Timezone.io
| 📅 Calendar ⚙️ Productivity | 🆓 Free |
Remote employees are spread across different time zones. Timezone.io helps you see all of your teammates’ time zones quickly in one visible chart.
Unique Benefit: For teams distributed across many time zones or who have a number of digital nomads switching time zones frequently, this helps to save time scheduling meetings and allows employees to protect their chosen work times.
Thank you Sonya Schwartz, Founder of Her Norm for sharing her favorite collaboration tool.
Visit The Website:
https://timezone.io/
WeekCal
| 📅 Calendar | 🆓 Free |
WeekCal is a calendar mobile app that integrates with all of your other calendar programs to give you one view of your week, month, or year.
Unique Feature: Save often used events as a template to save time on many recurring meetings, appointments, or reminders.
Thank you Bill Hess of the Maple Media for sharing his organization’s mobile apps.
Visit The Website:
https://www.weekcal.com/
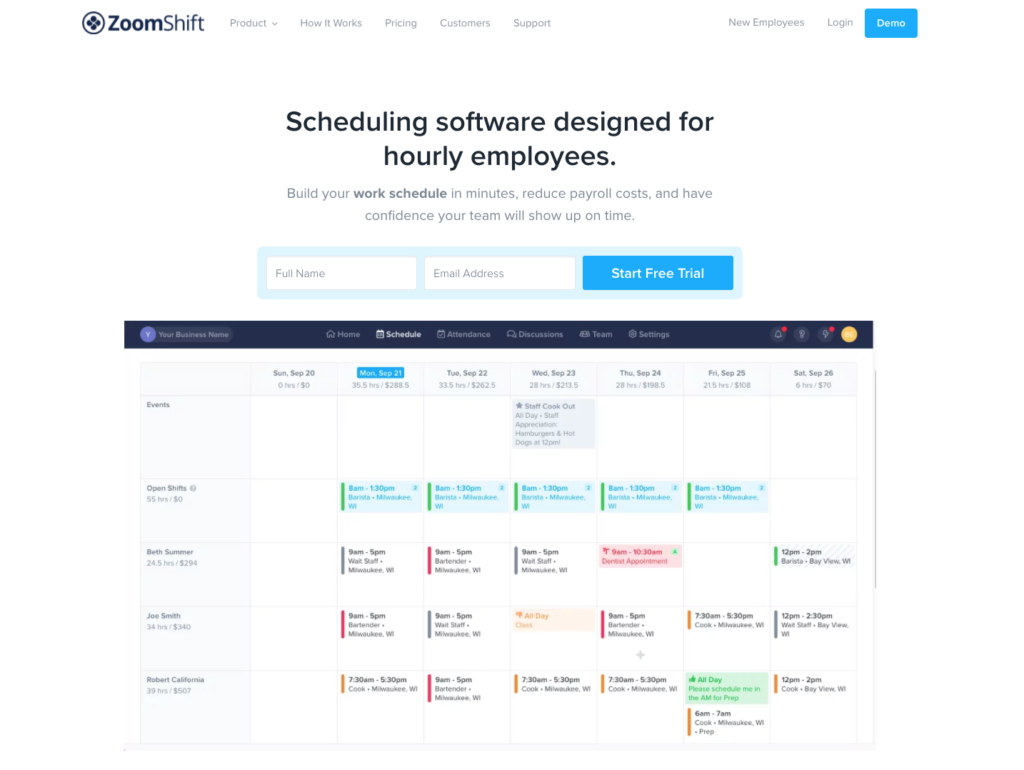
ZoomShift
| 📅 Calendar ⚙️ Productivity | 💰 Paid |
Whether you’re working remotely or on-site, you’ll need to ensure that there is always someone available for each shift. ZoomShift allows you and your employees to view shift calendars, set schedules in real time, and clock in either through the web or mobile app.
Unique Feature: ZoomShift offers a scheduling and timekeeping tool for small businesses. Using the mobile app, your workers can record their time as soon as they arrive at work without having to look for a physical time clock.
Visit The Website:
https://www.zoomshift.com/
💬 Chat
Here are the applications that are primarily categorized as chat tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
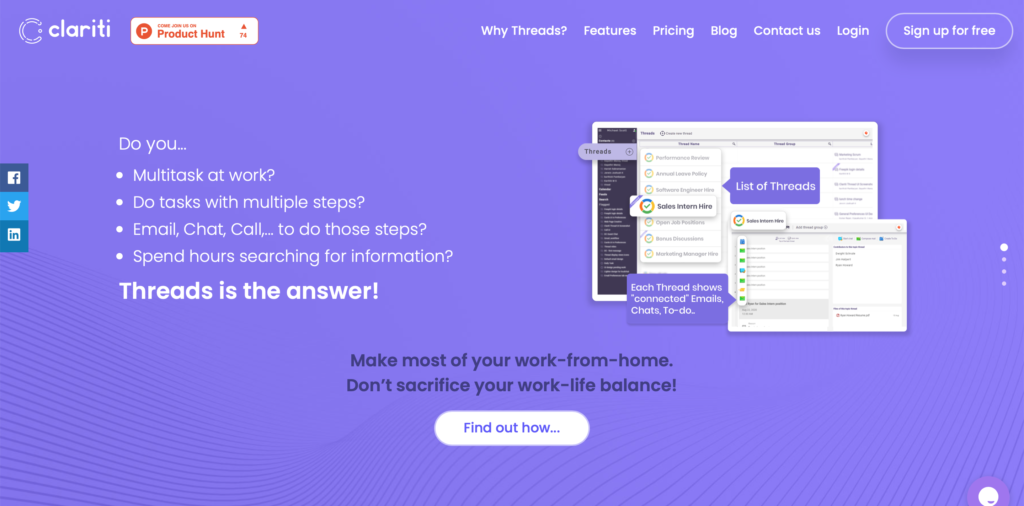
Clariti
| 🤝 Collaboration ⚙️ Productivity 📅 Calendar 💬 Chat | 💸 Freemium |
Clariti brings all communications to one place including emails, chats, documents, calls, social feeds, and to-dos, and automatically connects all related communications in topic threads.
Unique Feature: Clariti automatically connects all related emails, chats, documents, and social feeds on the same topic in an easy to use thread form. With Threads, there is no need to search for information across multiple apps as everything is connected in one place.
Thank you Vinay Wagle, VP Sales & Marketing, at CCE Technologies, Inc. for sharing his team’s software tool.
Visit The Website:
https://clariti.app
Flock
| 💬 Chat 🤝 Collaboration 🎥 Video | 💸 Freemium |
Flock is a chat platform with built-in video calls, and productivity tools (task lists, reminders, polls, etc.) all in one place.
Unique Benefit: “Voice Notes” is a feature that allows mobile users to send personalized voice notes rather than text.
Thank you to Rolf Bax of resume.io for sharing his favorite messaging and collaboration tool.
Visit The Website:
https://flock.com/
Mattermost
| 💬 Chat 🤝 Collaboration 🎥 Video 🔒 Security | 💰 Paid |
Mattermost is like Slack but hosted on your servers.
Unique Benefit: “This app is essential when self-hosting is a must for exchanging confidential information or protecting your conversations from third parties.”
Thank you David Morneau, CEO of inBeat, for sharing his remote team’s chat tool of choice.
Visit The Website:
https://mattermost.com/
Slack
| 💬 Chat 🤝 Collaboration 🔗 Automation 🎥 Video | 💸 Freemium 👍 Henry’s Favorite |
Slack is primarily a chat tool for teams, but also has video and voice calls, and many apps and bots that allow you to automate tasks and integrate with other tools you use.
Unique Benefit: The chat function is trendy and easy-to-use, but it’s a chat tool like many other. The real value in Slack comes through the apps and bots. Sales people can get notifications into Slack when a lead comes into their CRM system. You can integrate Slack with the task-list tool like Todoist or Trello. Set reminders for yourself that are recurring. That’s where all of the value comes in.
Thank you to Laura Fuentes of Infinity Dish and Jennifer Willy of Etia.com for sharing their favorite chat tool.
Visit The Website:
https://slack.com/
| 🎥 Video 💬 Chat ☎️ Phone | 🆓 Free |
WhatsApp is a simple messaging app with direct messages, groups, phone calls, and video calls that you can use on your phone or computer.
Unique Feature: WhatsApp for Business allows you to turn the app into a customer-facing interaction tool. You can post products and information about your business, and respond to messages from customers.
Thank you Tarah Darge, Marketing Manager at timetoreply, sharing her favorite remote chat tool.
Visit The Website:
https://www.whatsapp.com/
🤝 Collaboration Tools
Here are the applications that are primarily categorized as collaboration tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Blink
| 🤝 Collaboration ⚙️ Productivity 📅 Calendar 💬 Chat 🗂️ Document Management 👩💼 Human Resources (HR) | 💰 Paid |
Blink is a modern-day intranet that improves communication and productivity for remote teams. It offers a number of tools built-in: calendar management, discussion boards, chat, employee directory, news feeds, and more.
Unique Feature: The Content Management Hub allows you to organize, share, and search for all necessary documents across the organization like handbooks, processes, training, etc.
Thank you Sonya Schwartz, Founder of Her Norm for sharing her favorite collaboration tool.
Visit The Website:
https://joinblink.com/
Brosix
| 🤝 Collaboration 💬 Chat 🎥 Video | 💸 Freemium |
Brosix provides teams with a private communication network with encrypted instant messaging, video and audio chats.
Unique Feature: You control your own network hosted on Brosix servers, giving you full control over your internal communication while eliminating the need for extra hardware.
Thank you to Nikola Baldikov of Brosix for sharing his company’s messaging and collaboration product..
Visit The Website:
https://www.brosix.com/
Databox
| 🤝 Collaboration 🔗 Automation | 💸 Freemium 👍 Henry’s Favorite |
Databox pulls data from multiple sources into one, customizable dashboard tool so you can track business performance.
Unique Benefit: The key to a tool like Databox is which software tools you can easily integrate with. Databox has 70+ integrations, which will likely cover almost all of the connections you need to present business performance. Learn more in this Databox review.
Visit The Website:
https://databox.com/
FikaTime
| 🤝 Collaboration 👩💼 Human Resources (HR | 💰 Paid |
FikaTime is a Microsoft Teams bot to help teams feel socially-connected to each other and the organization by pairing employees for a coffee break.
Unique Benefit: It’s simple enough to stick and it helps companies invest in the relationship between team members where you can actually measure the impact of these activities.
Thank you to Jillian Reece of Behaviour Lab for sharing this collaboration tool for remote teams.
Visit The Website:
https://www.fikatime.app/
Flowdock
| 🤝 Collaboration 💬 Chat 🔗 Automation | 💰 Paid |
Flowdock gathers all integration updates in one space, so the team can save tons of time instead of searching for something all over the app. It also offers real-time team chat for the whole organization.
Unique Feature: The Integration Inbox allows you to view updates from each of your team’s software tools in one place.
Thank you Samantha Moss, Editor at Romantific for sharing her favorite remote work tool.
Visit The Website:
https://www.flowdock.com/
Glasscubes
| 🤝 Collaboration 📋 Project Management 💬 Chat | 💰 Paid 👍 Henry’s Favorite |
Glasscubes is a Sharepoint alternative that allows you to create online workspaces for communication, project management, file sharing, and client portals in one place.
Unique Benefit: Most collaboration tools stop with your employees. Glasscubes has a feature called “Client Portals” that allows you to benefit from collaboration with clients and external partners within the same tool you collaborate internally.
Visit The Website:
https://www.glasscubes.com/
Loop Team
| 🤝 Collaboration 🎥 Video 💬 Chat | 🆓 Free |
Loop Team is an office space recreated digitally. See what others are working on, join meeting rooms, and have one-one-one chats or discussions in one (currently free) tool.
Unique Feature: “Focus mode” is a feature that shows when teammates are in doing “Deep Work” so notifications won’t bug them.
Visit The Website:
https://loopteam.co/
Miro
| 🤝 Collaboration 🎥 Video | 💸 Freemium 👍 Henry’s Favorite |
Miro is a cloud-based, digital whiteboard with built-in video meeting capability and many white-boarding tools.
Unique Feature: Miro’s strategy template library has hundreds of templates to organized your meetings and brainstorming sessions. These templates are organized across strategy, planning, brainstorming, feedback, and more.
Thank you Marketa Machalkova, Community Manager of Hacker Paradise for sharing her team’s favorite collaboration tool.
Visit The Website:
https://miro.com
Mural
| 🤝 Collaboration 🎥 Video | 💰 Paid |
Mural is an online white boarding software.
Unique Feature: Mural has a number of integrations with other software tools like Microsoft 365, Dropbox, Slack, Google Drive, Trello, and Zapier. That integration engine allows you to quickly import documents from other tools, pull spreadsheet data into Mural sticky notes, and pull in Slack conversations into your whiteboard.
Thank you Drew Falkman of Modus Create for sharing his favorite remote whiteboard tool.
Visit The Website:
https://mural.co/
Notion
| 🤝 Collaboration ⚙️ Productivity 📋 Project Management 📅 Calendar 🗂️ Document Management | 💸 Freemium |
Notion is an all-in-one workspace where you can write, plan, collaborate and get organized in one tool through notes, tasks, projects, roadmaps, and more.
Unique Feature: “One of the great things about Notion is that it provides you with a set of building blocks to be able to create your own layouts and toolkit that works best for you and your team.”
Thank you Jase Rodley for sharing his favorite remote collaboration tool.
Visit The Website:
https://www.notion.so/
Plutio
| 🤝 Collaboration ⏰ Time Tracking ⚙️ Productivity 📋 Project Management 📅 Calendar | 💰 Paid |
Plutio is a tool to run your business – many of the individual tools you currently have built into one place.
Unique Benefit: With project management and time tracking in the same tool as proposals and invoices, you see a bunch of improvements in your process. You don’t have to connect different apps or copy data from one system to the other.
Thank you Aastha Shah, Senior Content Writer at Meetanshi, for sharing her favorite collaboration tool.
Visit The Website:
https://www.plutio.com/
Recess
| 🤝 Collaboration 👩💼 Human Resources (HR) | 💸 Freemium |
Recess is internal marketing communications software for internal company newsletters and announcements.
Unique Feature: “Company Engagement Stats” allows you to track employee happiness and engagement.
Thank you Chris Handy for sharing their team’s product.
Visit The Website:
https://www.recess.io/
Soapbox
| 🤝 Collaboration ⚙️ Productivity 📋 Project Management | 💸 Freemium |
Soapbox is a tool designed to drastically improve meetings. For one-one-one or team meetings, you can manage a shared agenda, take notes, assign goals and tasks that result from the meeting, and report on progress made.
Unique Feature: The Next Steps tracker allows for action items to live within the meeting agenda. Then, those items will be sent in meetings notes and through Slack messages.
Visit The Website:
https://soapboxhq.com/
Stackfield
| 🤝 Collaboration ⏰ Time Tracking 📋 Project Management 📅 Calendar | 💰 Paid |
Stackfield is a collaboration tool that allows you to communicate, manage tasks, and track time in one place.
Unique Benefit: “Thanks to end-to-end data encryption, as well as the usage of compliant with EU-GDPR and ISO-certified data centers, you do not have to worry about the cybersecurity of your company’s and your client’ data.”
Thank you Kenny Trinh, CEO of Netbooknews, for sharing his favorite remote collaboration tool.
Visit The Website:
https://www.stackfield.com/
Thoughtexchange
| 🤝 Collaboration | ❓ Unknown Price |
Thoughtexchange is a tool that allows you to gather answers to questions in real time from your employees or customers.
Unique Benefit: “Thoughtexchange lets business leaders crowdsource intelligence from the usually silent, overlooked majority in their teams to contribute ideas that help drive companies forward in an inclusive way.”
Thank you Michael Butcher of SJS Public Relations for sharing his favorite collaboration tool for business leaders.
Visit The Website:
https://www.thoughtexchange.com/
Whimsical
| 🤝 Collaboration | 💸 Freemium |
Whimsical is an online whiteboard software with built-in tools like wireframes, flowcharts, and mind maps.
Unique Feature: The Mind Map tool allows you to organize your brainstorming sessions in a hierarchy with the ability to stylize, link, comment on, and color code different elements.
Thank you Agnieszka Kasperek, CMO at Taskeo.co, for sharing her favorite whiteboarding tool.
Visit The Website:
https://whimsical.com/
Workast
| 🤝 Collaboration ⚙️ Productivity 📋 Project Management | 💸 Freemium |
Workast is a tool for Slack users designed to help your teams get more done. Create tasks and projects, manage meetings, create surveys, and more. Plus with plenty of integrations, and a freemium plan, you can’t go wrong with Workast.
Unique Feature:With the robust Slack integration you can create tasks, assign users, comment on tasks, complete tasks, and much more all without ever having to leave Slack.
Visit The Website:
https://workast.com
🗂️ Document Management
Here are the applications that are primarily categorized as document management tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
CocoFax
| 🗂️ Document Management 🤝 Collaboration | 💰 Paid |
CocoFax is online faxing service for business, which you can send and receive faxes without the requirement of a fax machine, phone line, or any other unnecessary hardware.
Unique Feature:You can send faxes from your computer or phone or as an attachment out of your email. If you are in a business that requires faxing, this is a great tool to modernize the process.
Thank you Carol Li of CocoFax for sharing the software tool her team has built.
Visit The Website:
https://cocofax.com/
Dropbox
| 🗂️ Document Management 🤝 Collaboration | 💰 Paid |
Dropbox is a primarily a file sharing tool with built-in content collaboration features.
Unique Benefit: Have you ever tried to figure out how to a large file over email? Dropbox allows you to share files much more easily than email.
Thank you Ryan Roller of the Bead The Change for sharing his organization’s document sharing app.
Visit The Website:
https://www.dropbox.com/
Google Drive (+ Docs, Sheets, Slides)
| 🗂️ Document Management 🤝 Collaboration | 💸 Freemium 👍 Henry’s Favorite |
Google Drive is a file and folder system that is saved through the cloud (accessible on the internet). Then, you can use Google Docs (like Microsoft Word on the internet) and Google Sheets (like Excel) to collaborate on work remotely.
Unique Benefit: The ability to edit a document or spreadsheet online is the biggest benefit. If you’ve been doing that through Microsoft Word then emailing versions back and forth, this would be a major upgrade to your process and productivity.
I don’t want to recommend this one, trust me. Google doesn’t need my help. But Drive (or something like it) is a must for remote teams. If you try to manage files and folders and collaborate on documents that are saved locally to employees’ computers, you’ll have no chance with a distributed team.
-Henry
Thank you to Majid Fareed, Digital Marketer at F Jackets, for sharing his team’s remote collaboration tool of choice.
Visit The Website:
https://www.google.com/drive/
Microsoft 365
| 🗂️ Document Management 🤝 Collaboration 📅 Calendar 🎥 Video 💬 Chat ☎️ Phone | 💰 Paid |
This is Microsoft Word, Powerpoint, Excel, Outlook, Teams, cloud storage and much more all in one. You also get the web versions of all of these tools so you can collaborate online.
Unique Benefit: You get about 95% of the tools you’ll use on a daily basis (Word, Excel, PowerPoint, Outlook, Calendar, Skype) all in one package. It really simplifies your expenses, logins, and your ability to share documents across tools. “Microsoft has been frequently releasing new features that have really improved Teams for collaboration. During a meeting you can work on in Excel, a Word doc or PowerPoint together within the meeting itself.
Thank you Chad Gniffke of briteCITY and Dave Spinelli of ANRO Inc. for sharing their team’s remote collaboration tool of choice.
Visit The Website:
https://www.microsoft.com/en-us/microsoft-365/business
ScanPro
| 🗂️ Document Management | 🆓 Free |
ScanPro scans any document into PDF format.
Unique Feature: You can send a fax from the mobile app for contracts, cancellations or confirmations, or other legally binding documents that require that format.
Thank you Bill Hess of the Maple Media for sharing his organization’s mobile apps.
Visit The Website:
https://scanproapp.com/
Traveling Mailbox
| 🗂️ Document Management | 💰 Paid 👍 Henry’s Favorite |
Traveling Mailbox gives you a physical address unique to your company, and then scans the outside of your mail into an online portal. You can then review your mail online and request mail you need to see to be opened and scanned.
Unique Benefit: If you have a remote team without a physical office, you need to have an address to at least offer a way to receive checks and bills. There are a lot of issues with choosing your home as your business address. If you like to travel, you’ll also need a good way to physically check your mail. Traveling Mailbox solves all of these issues and essentially turns your physical mail into an online tool accessible from anywhere.
Visit The Website:
https://travelingmailbox.com/
🪑 Equipment Management
Here are the tools to help you manage your physical equipment and infrastructure (office chairs, desks, computers, etc.) for remote employees. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Firstbase
| 🪑 Equipment Management | ❓ Unknown Price |
Set up, manage, maintain and retrieve all the physical equipment needed for your remote workers.
Unique Feature: Firstbase provides IT support for ongoing maintenance and repairs on hardware and software infrastructure.
Visit The Website:
https://www.firstbasehq.com/
Hofy
| 🪑 Equipment Management | ❓ Unknown Price |
Send, track and gather home office equipment for your remote employees.
Unique Feature: Companies can send custom-branded packaging and onboarding packs* for new joiners that will build brand pride at home.
Visit The Website:
https://www.hofy.co/
👩💼 Human Resources (HR) Tools
Here are the applications that are primarily categorized as HR and people tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Culture Amp
| 👩💼 Human Resources (HR) | ❓ Unknown Price |
Culture Amp is a platform that allows organizations to collect, understand, and act on employee feedback.
Unique Feature: The employee engagement survey tool comes with a library of research-backed questions and survey templates to choose from.Culture Amp is a platform that helps companies create and manage the culture, and improve employee engagement, retention and performance.
Thank you James Walsh of Billions In The Bank for sharing his favorite remote work tool.
Visit The Website:
https://www.cultureamp.com/
See Also: 25 Remote Team Management Tools
Deel
| 👩💼 Human Resources (HR) | 💸 Freemium |
Deel is a platform that helps companies manage international payroll, benefits, taxes, and compliance in 150 countries.
Unique Feature: Document Collection allows you to collect country-specific documents in over one hundred countries to stay on top of local laws.
Visit The Website:
https://www.letsdeel.com/
Gusto
| 👩💼 Human Resources (HR) ⏰ Time Tracking 🗂️ Document Management | 💰 Paid 👍 Henry’s Favorite |
Gusto is a cloud-based payroll, benefits, and HR platform.
Unique Feature: Gusto’s hiring and onboarding tools allow you to turn documents (like offer letters and employee handbooks) into templates you can assign to the new hire to review and sign. You can manage a task list for onboarding and give access to benefits and HR tools within Gusto.
Gusto is a fantastic tool and company. It’s what we I use. Gusto rolled out features within weeks to help support small businesses through the Paycheck Protection Program (PPP) loans in the spring of 2020. They do this over and over, adding value whenever things change in payroll, taxes, or the policy.
-Henry
Visit The Website:
https://gusto.com/
Lattice
| 👩💼 Human Resources (HR) 🤝 Collaboration | 💰 Paid |
Lattice is a people management platform that has features to help track employee engagement, career advancement, people surveys, and more.
Unique Feature: “Lattice helps you set growth goals and track individual performance for remote workers. You need a proper framework to understand how someone is progressing in their work, and Lattice is a great platform to keep track of this and make it transparent.”
Thank you Neal Taparia of Solitaired for sharing his favorite remote work tool.
Visit The Website:
https://lattice.com/
Remote
| 👩💼 Human Resources (HR) 💰 Payroll ✅ Compliance | 💸 Freemium 👍 Henry’s Favorite |
Remote an employer of record built for distributed teams working across many countries. The tool brings international payroll, benefits, taxes, and compliance all into one place.
Unique Feature: Remote currently works in 200+ countries as of July 2024.
Visit The Website:
https://remote.com
Vacation Tracker
| 👩💼 Human Resources (HR) | 💰 Paid |
Vacation Tracker is a Slack plugin that helps employees and companies with leave management.
Unique Benefit: “All employees have to do is to type “/vacation” in their Slack account, and it schedule leaves immediately. They can also see how many days off they used and choose among more than nine leave types. Managers are instantly notified whenever someone makes a request.”
Thank you Nikolina Jeric, Founder of 2Date4Love.com for sharing her favorite leave management tool.
Visit The Website:
https://vacationtracker.io/
Workable
| 👩💼 Human Resources (HR) | 💸 Freemium 👍 Henry’s Favorite |
Workable is a talent acquisition software. It allows you to attract job candidates, manage the entire hiring process, and report on how it went.
Unique Feature: “Custom Pipelines” allow you to build the hiring process you want and then manage each candidate through every step. You can use email templates to send one-one-one or in bulk based on the stage of the pipeline. You can pass candidates onto your team members to review. Then, you can report on metrics for each stage.
Workable is an amazing well designed, functional software. I’ve tried to manage this process in Excel spreadsheets, through the backend of job boards, and through a marketing software we tried to bend for hiring. At Nectafy, the marketing agency I work for, we were able to bring the average time it took from application to offer from 60 days to 18. This is the best tool for your hiring process, period.
-Henry
Visit The Website:
https://www.workable.com/
☎️ Phone Systems
Here are the applications that primarily help with your phone systems and calls. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Grasshopper
| ☎️ Phone | 💰 Paid |
Grasshopper is a virtual phone system that gives you a business line that forwards calls to your personal phone and voicemails to your email. It’s a phone system for a distributed team.
Unique Feature: Voicemail transcription converts voicemails into text so you can read them online, in your app, or over email.
Visit The Website:
https://grasshopper.com/
⚙️ Productivity Tools
Here are the applications that are primarily categorized as productivity tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Evernote
| ⚙️ Productivity 🤝 Collaboration | 💸 Freemium 👍 Henry’s Favorite |
Evernote is a note-taking app that allows you to organize and share notes, scan documents, manage to-do lists, and more.
Unique Feature: As simple as it sounds, the search function is a game changer. If you take notes by hand, you know you have to search notebooks manually. Evernote opens a whole new world when you can search a word and pull up your exact note from months or years ago.
I’ve used this for years. This is one of the most important tools in my remote toolkit.
– Henry
Visit The Website:
https://evernote.com/
EmailAnalytics
| ⚙️ Productivity | 💰 Paid |
EmailAnalytics is a productivity tool that visualizes employee email activity. You can measure metrics like average email response time, email traffic by hour of the day, and email traffic volume by day of the week.
Unique Feature: Average email response time is automatically captured and reported on in real-time. This is a key metric for sales and customer service teams in particular.
Thank you Jayson DeMers, CEO of EmailAnalytics, for sharing the productivity tool his team built.
Visit The Website:
https://emailanalytics.com/
Focusmate
| ⚙️ Productivity | 💸 Freemium |
Focusmate is a virtual coworking tool that pairs you up with an “accountability partner” so you can both encourage each other to get done what you set out to do during the session.
Unique Benefit: “Having someone challenging me to work (when I should be) motivates me since I have a goal to attain. The fact that these are strangers ensures I don’t get accustomed to anyone – every new session is unique.”
Thank you James Jason of Mitrade for sharing his favorite productivity tool.
Visit The Website:
https://www.focusmate.com/
Habitica
| ⚙️ Productivity | 💸 Freemium |
This app turns a to-do list into a game, where you have a character that levels up when you complete a task. You can add colleagues and fight monsters together. If you finish the tasks on time, you earn in-game Gold to buy custom rewards.
Unique Benefit: “We love using Habitica to add fun and motivation into managing our short-term tasks.”
Thank you David Morneau, CEO of inBeat, for sharing his remote team’s chat tool of choice.
Visit The Website:
https://habitica.com/
Holopod
| ⚙️ Productivity 📅 Calendar | 🆓 Free |
Holopod is a Slack plug-in that allows you to automatically update your status to block out the noise and deliberately plan uninterrupted blocks of time.
Unique Feature: Get a daily report that breaks down how you spend your time, and rate your days to get a clear picture of your work happiness.
Thank you Ablorde Ashigbi CEO at 4Degrees for sharing his favorite productivity tool.
Visit The Website:
https://holopod.com/
Mailbutler
| ⚙️ Productivity 🔗 Automation | 💸 Freemium |
Mailbutler is an email productivity extension for Apple Mail, Gmail and Outlook that allows people to manage their email in a flexible and easy way.
Unique Feature:“Send later” allows you to draft your email now and schedule it to be sent automatically later.
Thank you Tiffany Schwarz, Marketing Manager of Mailbutler, for sharing her company’s email plugin tool.
Visit The Website:
https://www.mailbutler.io/
Milanote
| ⚙️ Productivity 🗂️ Document Management | 💸 Freemium |
Milanote lets you upload files, track to-do lists and tasks, save images, videos and more. All of your content can live in one secure place, side by side.
Unique Feature: Arrange your notes side by side with images, links and more.
Visit The Website:
https://milanote.com/
Timetoreply
| ⚙️ Productivity | 💰 Paid |
Timetoreply is a software tool that tracks email reply times, volumes, contact success rates, emails missing replies as well as general productivity (time of first and last activity).
Unique Feature: Set response time goals and reward staff based on their activity and email reply times.
Thank you Tarah Darge of Timetoreply for sharing her company’s email productivity tool.
Visit The Website:
https://timetoreply.com/
Todoist
| ⚙️ Productivity | 💸 Freemium |
Todoist is a task-list app with advanced features to manage your productivity and share tasks with team members.
Unique Feature: You can add tasks to your Todoist application simply by emailing them to Todoist as tasks or comments. That’s a quick way to get tasks out of email and into one central location.
Visit The Website:
https://todoist.com/
See Also: 7pace has a good list of productivity tools for developers.
📋 Project Management Tools
Here are the applications that are primarily categorized as project management tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Teamwork
| 🤝 Collaboration ⏰ Time Tracking 📋 Project Management 📅 Calendar 💬 Chat | 💸 Freemium 👍 Henry’s Favorite |
A platform built primarily for teams that do client work, Teamwork has all the bells and whistles to do great project management the way you want.
Unique Feature: “Workload” gives you a quick overview of everyone’s capacity, so you can deliver projects on time and on budget.
Visit The Website:
https://teamwork.com
Asana
| 📋 Project Management ⚙️ Productivity 📅 Calendar | 💸 Freemium |
Asana is an agile project management software that allows teams to collaborate, and manage and track tasks.
Best Feature: “My favorite feature is that the software is customizable to any team’s needs. I use it to set tasks, projects, and timeline and to generate comprehensive project reports.”
Thank you Vincent Scaramuzzo (President of Ed-Exec), Allan Borch (Founder of Dotcom Dollar) and Jacob J. Sapochnick (Attorney) for sharing their favorite project management tool for remote work.
Visit The Website:
https://asana.com/
Basecamp
| 📋 Project Management ⚙️ Productivity | 💰 Paid | 👍 Henry’s Favorite |
Basecamp is a project management tool that organizes work into separate projects. Each project holds all tasks, discussions, documents, dates and people in one place.
Unique Benefit: The flexibility allows us to “use it for knowledge management and as an internal blog. We can announce important company updates and write about what’s going on with the company and our product. With a remote team, it’s crucial to keep everyone on the same page.”
Thank you Petra Odak, CMO of Better Proposals, for sharing her favorite remote tool.
Visit The Website:
https://basecamp.com/
ClickUp
| 📋 Project Management 🤝 Collaboration ⏰ Time Tracking | 💸 Freemium |
ClickUp is an all-in-one project management tool built for marketing companies.
Unique Feature: Resource Management allows you to manage workload and timelines for your entire team.
Thank you Angela Mangrum of Mangrum Career Solutions, Recruitment Specialists, for sharing this remote work tool.
Visit The Website:
https://clickup.com/
Favro
| 📋 Project Management 🤝 Collaboration | 💰 Paid 👍 Henry’s Favorite |
Favro is a project management tool that can be configured in a number of ways (Kanban, timeline, checklists, burndowns, etc.)
Unique Feature: The backlog allows you to assign tasks up to a certain limit. For example, if need to deliver 100 “points” for a client in a given month, you can assign point values to each task until you reach 100. It helps to manage priority, profitability, and workload.
Visit The Website:
https://www.favro.com/
Indy
| ⏰ Time Tracking 📋 Project Management 🗂️ Document Management | 💸 Freemium |
Indy is an all-in one management software that helps freelancers and small businesses track everything from proposals to payments. Indy makes organization and time management easy
Unique Feature: There are no hidden costs or fees: everything is included in a low monthly fee. You can join for free and start using all of the features up to a limit. Then, you get unlimited access to the Indy pro bundle for $12 per month.
Visit The Website:
https://weareindy.com
Infinity
| 📋 Project Management 🤝 Collaboration 📅 Calendar | 💰 Paid |
Infinity is a project management and work management software with a number of versatile features: tables, Gantt Charts, forms, lists, and more.
Unique Benefit: Infinity is an all-in-one project management tool like Trello, Asana, and Monday.com. The main benefit is the drastic difference in price. Infinity will cost you $149 per year for 10 users vs. the other ones mentioned that would all be over $1000 per year.
Thank you Branka Vuleta, Founder of LegalJobSite, for sharing her team’s favorite remote work tool.
Visit The Website:
https://startinfinity.com/
Jira
| 📋 Project Management 🔗 Automation | 💸 Freemium |
Jira is an agile project management tool built for software development teams.
Unique Feature:The Jira Scrum Board brings together software development teams on one overarching goal, then breaks up each task into smaller tickets that incrementally push the project toward its end goal.
Thank you Azza Shahid of InfiniteRecovery for sharing her team’s agile project management tool of choice.
Visit The Website:
https://www.atlassian.com/software/jira
Monday.com
| 📋 Project Management 🤝 Collaboration 🔗 Automation 📅 Calendar ⏰ Time Tracking | 💰 Paid |
This project management tool enables teams to quickly add members, assign tasks, customize workflows, and track the progress of a project. For more information, read our monday.com review here.
Unique Feature: Monday.com has its own app marketplace that allows outside people to build custom tools into the software. Developers can build private apps just for the benefit of their team, or build and sell public apps that other organizations to benefit.
Thank you Marketa Machalkova, Community Manager of Hacker Paradise for sharing her team’s favorite collaboration tool.
Visit The Website:
https://monday.com/
Paymo
| ⏰ Time Tracking 📋 Project Management | 💸 Freemium |
Paymo is a modular project management tool designed for creative agencies and anyone who sells hour of their work.
Unique Feature: A built-in accounting module allows you to send proposals, turn timesheets into invoices, track expenses, and get paid online easily and quickly.
Visit The Website:
https://www.paymoapp.com/
ProofHub
| 📋 Project Management 📅 Calendar 🎥 Video | 💰 Paid |
ProofHub is a project management tool loaded with features. It’s a good fit for complex teams.
Main Benefit: “It comes with options for creating multiple workflows for complex teams, a quick discussion feature that I use to touch base with both clients and my remote team, an integrated group chat feature, and a powerful project reports generator.”
Thank you to Paul French, Managing Director of Intrinsic Search, for sharing his team’s favorite project management tool.
Visit The Website:
https://www.proofhub.com/
Trello
| 📋 Project Management 🔗 Automation | 💸 Freemium |
Trello is a simple, digital version of a Kanban board–a project management method.
Main Benefit: “Trello allows your team to see what tasks they need to do, tick off the boxes as they do them, then give a clear, visual indication when a task is finished. Other team members can see the progress on tasks, so there’s no danger in stepping on toes or wondering about the status of a task.”
Thank you Dan Bailey (President of WikiLawn), Jessica Wise (Marketing Manager at HelpSquad), and Michael Hammelburger (CEO at Expense Reduction Group), and Fred Blair (Founder of AwesomeHoops.com) for sharing Trello.
Visit The Website:
https://trello.com/
Wrike
| 📋 Project Management | 💸 Freemium |
Wrike is a digital work management tool that lets users track and coordinate projects, combining a simple user experience and interface with enough depth for power users.
Main Benefit: “Faster Productivity With Powerful Work Management. With a universal work management process that covers everything, wall to wall, Wrike Lightspeed has all the features you need.”
Visit The Website:
https://wrike.com/
🔒 Security Tools
Here are the applications that primarily help with cybersecurity. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
Axis Security
| 🔒 Security | ❓ Unknown Price |
Employees need easy access to critical applications and resources, wherever they are, to keep the business going. Axis delivers secure, easy-to-use, zero-trust access to business apps and resources for all employees everywhere.
Visit The Website:
https://www.axissecurity.com/
Dashlane
| 🔒 Security | 💸 Freemium |
Dashlane securely creates strong and random passwords, then stores and auto-fills them when you log into your online accounts. This is a direct competitor to LastPass and 1Password.
Unique Feature:You can store credit card information and auto-fill those details whenever you checkout online.
Thank you Marketa Machalkova, Community Manager of Hacker Paradise for sharing her team’s password storage tool.
Visit The Website:
https://monday.com/
1Password
| 🔒 Security | 💸 Freemium 👍 Henry’s Favorite |
1Password allows you to save all of your passwords and logins in one place behind your one master password. This is a direct competitor to Dashlane (see above) and Lastpass (which had a very public, nasty security breach in 2022).
Unique Feature: As you set up new online accounts, the 1Password browser extension pops up to allow you to create a secure, randomly created password.
Visit The Website:
https://1password.com/
⏰ Time Tracking Tools
Here are the applications that are primarily categorized as time tracking tools. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
DueFocus
| ⏰ Time Tracking ⚙️ Productivity | 💸 Freemium |
DueFocus is a time tracking tool with built-in productivity and performance reporting.
Unique Feature: The “Focus” tool helps you control distractions by providing personal metrics around where you spend your time.
Thank you Shiv Gupta, CEO of Incrementors Web Solutions, for sharing his favorite remote work tool.
Visit The Website:
https://duefocus.com/
Everhour
| ⏰ Time Tracking 📋 Project Management | 💸 Freemium |
Everhour is a time tracking, budgeting, and invoicing tool that integrates with popular project management tools.
Unique Feature: Integrate Everhour with tools like Asana, Trello, and Basecamp so you can time track within those tools without having to log out or open a new tab.
Thank you Joe Flanagan of 90s Fashion World for sharing the time tracking tool he uses with his editorial team.
Visit The Website:
https://everhour.com/
Hubstaff
| ⏰ Time Tracking ⚙️ Productivity | 💸 Freemium |
HubStaff is an all-in-one tool for time tracking, productivity analysis, invoicing, and payroll.
Unique Benefits: “What makes it especially unique is that the Hubstaff team runs on its own platform, using the products to build and improve the products, every day. Hubstaff has over 34,000 business customers and is still run 100% remote by a team of 60” – Dave Nevogt.
“I can see what my employees are up to with just a glance on their dashboard, and they can easily clock in and out of the app” – Dennis Bell.
Thank you Dave Nevogt (CEO and Co-founder of Hubstaff), Ajmal Dar of Moccasin Guru, and Dennis Bell of Byblos Coffee for sharing their favorite remote work tool.
Visit The Website:
https://hubstaff.com/
Intervals
| ⏰ Time Tracking 📋 Project Management 📅 Calendar | 💰 Paid |
Intervals is a time tracking tool that is best for IT companies, web developers and software companies.
Unique Feature: IT project management for bug tracking and milestone tracking. “I can say that Intervals made a massive contribution to our productivity and business advancement.”
Thank you to Karl Armstrong, Founder of EpicWin App, for sharing his team’s time tracking and project management tool.
Visit The Website:
https://www.myintervals.com/
Time Doctor
| ⏰ Time Tracking ⚙️ Productivity | 🆓 Free |
Time Doctor is time tracking and productivity tool for remote teams and freelancers.
Unique Feature: It helps you to track exactly where time was spent each day, and analyze which websites and applications were used on your computer. It also has a cool feature that gives users a friendly nudge when it detects that you might be distracted by a less productive task.
Thank you Tope Longe of the Running Remote Conference for sharing his favorite remote work tool.
Visit The Website:
https://www.timedoctor.com/
Toggl Track
| ⏰ Time Tracking | 💸 Freemium 👍 Henry’s Favorite |
Toggl Track is a simple time tracking web or mobile application with reporting, calendar integrations, and more.
Unique Benefit: I’ve used this tool for a few years with my small team at Nectafy. For small teams (five people or fewer), the Toggle Track free version is totally useful for simple time tracking needs at no cost.
Thank you to Domantas Gudeliauskas of Zyro for sharing their favorite time tracking tool for remote teams.
Visit The Website:
https://toggl.com/track/
Top Tracking
| ⏰ Time Tracking | 🆓 Free |
Top Tracking, by Toptal, is a time tracking software tool with screenshots and invoice processing with no-fee payments.
Unique Feature: In the “free basic version that records screenshots of your remote worker’s screen and saves it for your review later. This permits you to easily verify that your worker is focused on the tasks you have assigned.”
Thank you Jessica Rose, CCEO of Copper H2O, for sharing her favorite time tracking tool for remote teams.
Visit The Website:
https://www.toptal.com/tracker
timegram
| ⏰ Time Tracking ⚙️ Productivity 📋 Project Management | 💸 Freemium |
Timegram is a time tracking and project planning tool that allows businesses to manage and enhance the productivity of remote and hybrid teams. You can see team and individual productivity, plan projects, measure performance, track billable hours, and do so much more.
Unique Feature: “Timegram adheres to a zero-surveillance policy that respects employee privacy by not taking screenshots or webcam shots, or tracking mouse movements and keystrokes.”
Visit The Website:
https://www.timegram.io/
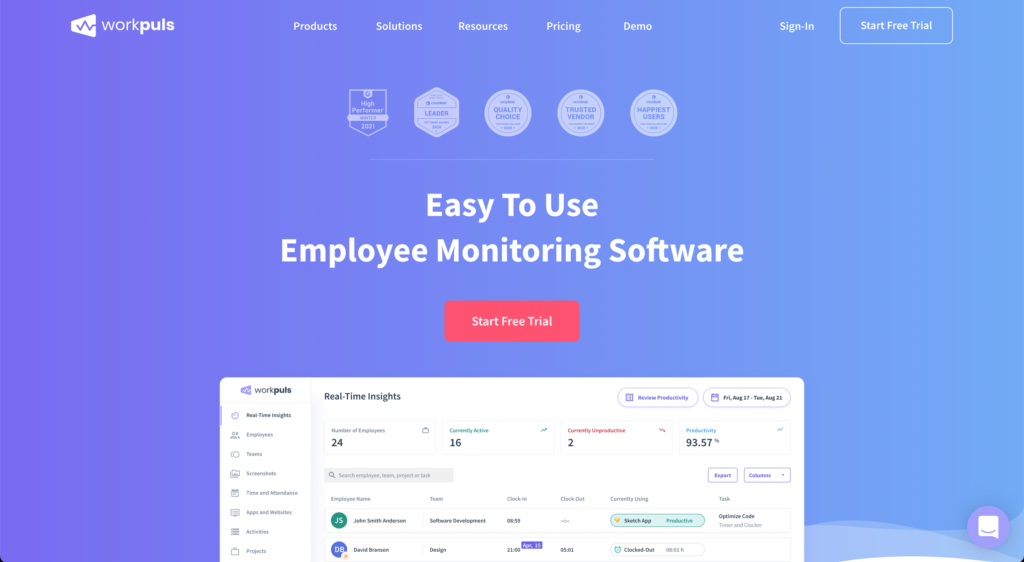
Workpuls
| ⏰ Time Tracking ⚙️ Productivity | 💰 Paid |
Workpuls is a productivity and analytics tool that helps remote organizations and freelancers boost productivity by surfacing work behavior patterns and insights. The core features include time tracking and automatic time mapping for budgeting.
Unique Feature: Workpuls automates employee clock ins, clock outs and the precise tracking of overtime hours by monitoring computer activity.
Thank you Blake Miner of the FlaneurLife.com for sharing his favorite remote work tool.
Visit The Website:
https://www.workpuls.com/
🎥 Video Tools
Here are the applications that are primarily help with video recording and meetings. If you don’t see any, we don’t have one that fits your filters. Recommend one to us here!
GoToMeeting
| 🎥 Video | 💰 Paid |
GoToMeeting is an online meeting and webinar software.
Unique Feature:“Call Me” allows you to call participants so they can log in with one click. This helps eliminate the long phone numbers and code entering to dial-in to a typical meeting.
Thank you Jeremy Ong of Hustlr for sharing his team’s favorite video conferencing tool.
Visit The Website:
https://www.gotomeeting.com/
Grain
| 🎥 Video | ❓ Unknown Price |
Grain is build for transcribing, trimming, and sharing highlights of Zoom calls.
Unique Feature: Grain is an easy way to grab just the most important parts of a recorded video meeting. This helps you cut down on the number of attendees required, stops the meeting summary emails, and enables you to pull out highlights to use internally or in your marketing.
Thank you Jeff Hardison of Grain for sharing his company’s remote video capture tool. If you’d like to learn more about using video in your business, particularly for marketing click the link.
Visit The Website:
https://grain.co/
Loom
| 🎥 Video | 💸 Freemium |
Loom enables you to quickly share your screen or browser, talk over it (including with a camera so you can be visible if you choose), and send that off to others with a link.
Unique Feature: “Instant sharing” lets you hit stop and automatically create a link that is copied to your clipboard to share. “We like it because it gives us the communication benefits of video, but without us having to schedule and organize meetings
in a more formal way” – Jenna, Music Grotto.
Thank you Ablorde Ashigbi CEO at 4Degrees for sharing his favorite video tool. Thank you to Jenna Carson, HR Manager at Music Grotto, for sharing how her team benefits from using Loom.
Visit The Website:
https://www.loom.com/
Skype
| 🎥 Video 💬 Chat ☎️ Phone | 🆓 Free |
Skype is for communication through instant messages or quick video calls and chats. It’s a faster way of communication to get an answer to a simple question.
Unique Feature: Live subtitles allow you to read the words that are spoken during an audio or video call.
Thank you Dennis Bell of Byblos Coffee for sharing his favorite tool for quick, remote communication.
Visit The Website:
https://www.skype.com/
Teleport
| 🎥 Video | 💸 Freemium |
Teleport is a lesser known video conferencing tool, but can be compared directly to Zoom or GoToMeeting.
Thank you Fraser Wilson of AnswerConnect UK for sharing his favorite video conferencing tool.
Visit The Website:
https://teleport.video/
The Echo
| 🎥 Video | ❓Unknown Price |
The Echo is a virtual experience tool for events, meetings, presentations, and one-on-one interactions online.
Unique Feature: Customizable avatars allow you to choose how you present, interact, and speak at the virtual event.
Thank you Ryan Costello, Founder and CSO of Event Farm, for sharing his team’s remote work tool.
Visit The Website:
https://www.eventfarm.com/the-echo
Zoom
| 🎥 Video ☎️ Phone | 💸 Freemium | 👍 Henry’s Favorite |
Zoom is a cloud-based meeting software (audio, video, screen-sharing, chat, and webinars) you can access from a computer or phone.
Unique Feature: Virtual backgrounds allow you to pick an image or video to go behind you, or to blur or touch up your appearance. This is helpful if you’re working from your kitchen or a guest bedroom or the road. But keep in mind! We’re advocates of the Anyvoo physical backdrop at Buildremote.
Visit The Website:
https://zoom.us/
Some background on this list of remote tools
I asked over 80 people to share the best remote tool they use while working from home or managing a remote team. Multiple people shared the same tool, so that’s why you see the 79 tools in the final list. Thank you to all of the contributors to this list.
Here’s how I went about organizing the different filters:
- I want remote tools that help with… These are the product categories. Each remote tool can have multiple categories. For example, Skye is a video and a chat tool all in one. When you view each product description, we list the primary category first and the secondary ones next.
- I’d like them priced in this way… These are our pricing categories:
- Free: The tool is completely free to use (they must have some other way to make money, or they aren’t making money. Either way, take advantage!)
- Freemium: There is a free option with limited features. Then, there are paid packages that open up more functionality. Don’t confuse this with free trials! Just about every tool on this list offers a free trial, but that doesn’t mean they are free or freemium.
- Paid: There are only paid packages (not free ones). These tools will likely have a free trial, but once that is up, they cost at least a $0.01 each month.
- Unknown: The tool has been recommended to us by one of the contributors, but the company’s website does not list pricing.
- I want to see only Henry’s favorites… These are tools that I personally rely on to work from home and run a remote company. If I’m still using them, that means they are my favorites (since I’ve tried and gotten rid of a number of them in the past). I update the list when I add or remove an app from my remote toolset.
Want to add a remote software tool to the list?
Fill in the form on this page. Then, I’ll take a look at the company’s website to see if it’s a good fit for this post. If it is, I’ll email you back asking for more details.




Great article, thanks! I use a number of these already. I filled out the form to include a VPN that my team and I use. I hope you’ll add it to the list.
we’ve started to work with tldv and it’s been great. was missing this here!
Thanks For Sharing The Remote Work Tools List Really Helpful and Great List Keep it up.
Fantastic roundup of remote work software! 🚀 Your detailed insights and categorization make it easy to find the perfect tools. Kudos for covering both popular and lesser-known options. Great resource for anyone diving into the remote work landscape.
Such a great read, learned something new today.